

Ransomware continues to pose a formidable threat to organizations, as cybercriminal activity persists unabated. Recent reports from the cyber insurance sector highlight the escalating menace, urging companies to intensify their defense strategies.
The modus operandi of ransomware attacks typically involves a threat actor infiltrating an organization’s system, seizing control of sensitive data, and then extorting payment under the threat of public disclosure. This has been a significant concern, especially over the past five years.
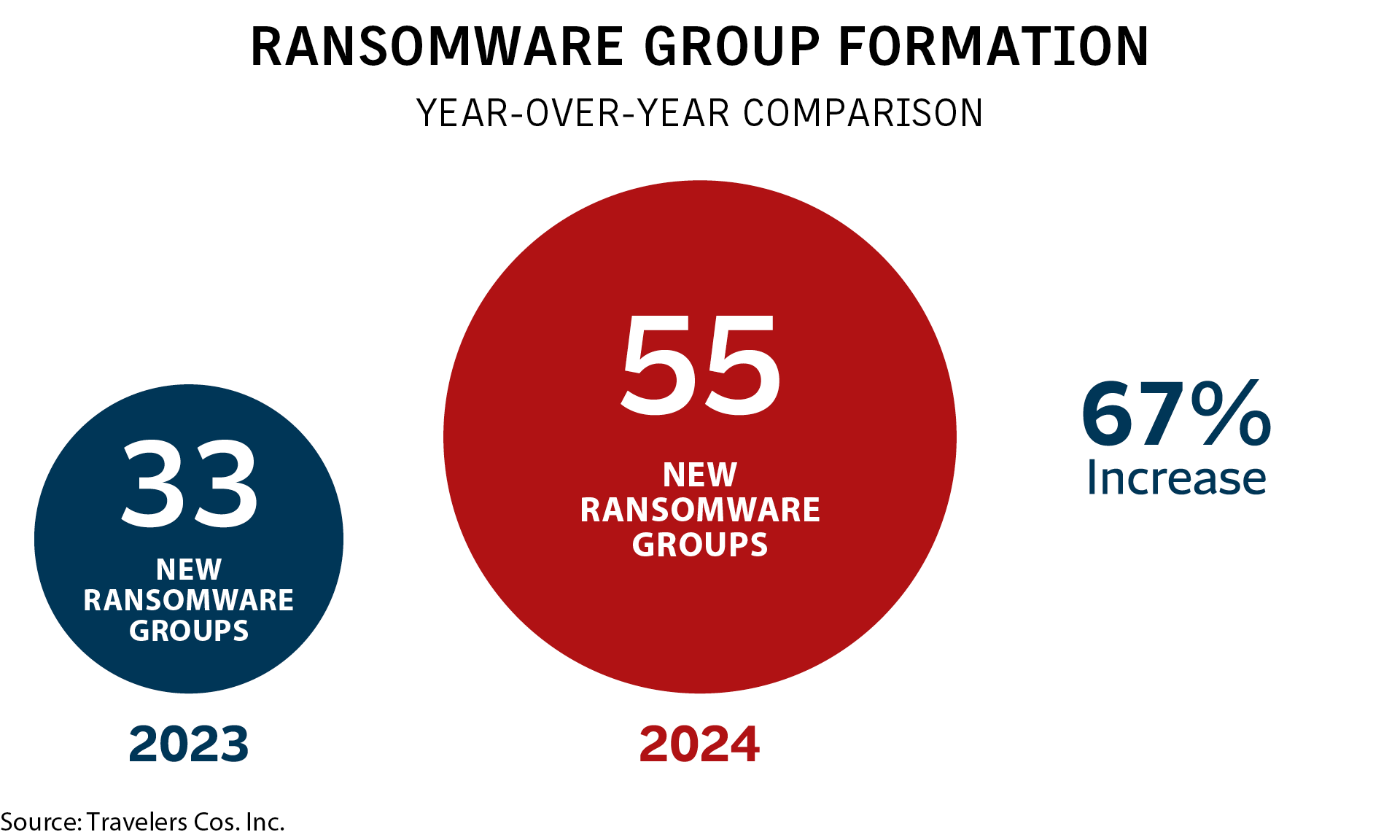
Data from a study by Travelers Cos. Inc. reveals a staggering 67% surge in the emergence of new ransomware groups last year. The final quarter witnessed the most intense leak site activity in over a year, according to Lauren Winchester, the Philadelphia-based head of cyber risk services at the insurer.
“Our analysis of ransomware leak site activities shows a consistent quarterly rise, with Q4 of 2024 witnessing a 32% increase over the previous quarter. It marked the highest leak site activity in 15 months, affecting nearly 1,700 companies,” noted Ms. Winchester. The activation of ransomware groups on leak sites has also seen a rise over the past year, she added.
In a March report, cyber insurer Coalition Inc. predicted that over 45,000 software vulnerabilities would be published this year. The most prevalent initial access methods for ransomware claims in 2024 were stolen credentials at 47%, followed by software exploitation at 29%.
“This issue is not fading away,” remarked Daniel Woods, a senior security researcher for Coalition based in Edinburgh, Scotland, who also lectures at the University of Edinburgh. In some instances, a security breach can extend its impact beyond the primary target, affecting ancillary victims.
“The repercussions ripple through society… It’s not merely one company suffering in some scenarios,” Mr. Woods explained.
Organizations can deploy several defenses against these attacks. Brute force attacks, where a threat actor attempts to breach a data system by randomly guessing passwords, can be thwarted by adopting multifactor authentication, which adds an extra verification step post-password. However, Mr. Woods cautions that this must be correctly implemented at suitable system points for efficacy.
Implementing controls like multifactor authentication can entail a significant financial outlay, potentially recurring if a business licenses a software product, according to Gwenn E. Cujdik, Exton, Pennsylvania-based manager of North American cyber incident response and cyber services for Axa XL. These costs can often exceed the means of small to medium-sized enterprises, she noted.
Training programs are also effective, Ms. Cujdik said. “Helping your employees better identify phishing attacks and developing policies and procedures for technology application software usage can significantly mitigate cyber exposures,” she explained. “These policies and procedures are not expensive.”
The initial step should be to recognize and comprehend the exposure, which not all businesses have done, Ms. Cujdik added. “From small enterprises to large corporations, some have convinced themselves that they don’t require cyber insurance,” she stated.
Endpoint detection and response is another technology tool that can aid businesses in combating ransomware, according to Ms. Winchester. By monitoring each user or endpoint on a network for suspicious activity, this technology can trigger alerts and help contain the progression of any breach incident or “minimize the blast radius,” she said.
Scanning for unprotected network elements that could be easily exploited can also assist organizations in mitigating ransomware threats, Ms. Winchester advised.
SİGORTA
6 saat önceSİGORTA
2 gün önceSİGORTA
2 gün önceDÜNYA
11 gün önceSİGORTA
15 gün önceSİGORTA
15 gün önceSİGORTA
15 gün önce 1
Elon Musk’s Father: “Admiring Putin is Only Natural”
11399 kez okundu
1
Elon Musk’s Father: “Admiring Putin is Only Natural”
11399 kez okundu
 2
Minnesota’s Proposed Lifeline Auto Insurance Program
9341 kez okundu
2
Minnesota’s Proposed Lifeline Auto Insurance Program
9341 kez okundu
 3
Introducing Vivo Y300 Pro+: A Blend of Power and Affordability
7293 kez okundu
3
Introducing Vivo Y300 Pro+: A Blend of Power and Affordability
7293 kez okundu
 4
What’s the best car insurance for seniors?
5954 kez okundu
4
What’s the best car insurance for seniors?
5954 kez okundu
 5
American Nurse Survives Harrowing Moped Crash in Thailand
2177 kez okundu
5
American Nurse Survives Harrowing Moped Crash in Thailand
2177 kez okundu
Veri politikasındaki amaçlarla sınırlı ve mevzuata uygun şekilde çerez konumlandırmaktayız. Detaylar için veri politikamızı inceleyebilirsiniz.